Knox Deep Dive: Real-time Kernel Protection (RKP)
The Knox platform’s patented Real-time Kernel Protection (RKP) is the industry’s strongest protection against kernel threats and exploits. RKP works seamlessly out-of-the-box, with no setup required. Simply powering on a Samsung Knox device provides world-class threat protection and attack mitigation. RKP supports the rest of the Knox security offerings to provide full security coverage without the typical gaps anticipated with mobile devices.
Why does kernel protection matter?
Kernel protection is central to device security and enterprise data protection.
A compromised kernel can leak sensitive data and even allow remote monitoring and control of the affected device. Other more commonplace protections like Secure Boot or hardware-backed keystores are of little value if the kernel itself is compromised at runtime. After a device boots and decrypts sensitive content, a kernel compromise can result in data leaks that directly impact an enterprise’s data integrity.
RKP design and structure
As part of the Knox platform’s security offerings, RKP employs a security monitor within an isolated execution environment. Depending on the device model, either a dedicated hypervisor or the hardware-backed secure world provided by ARM TrustZone technology provides the isolated execution environment.
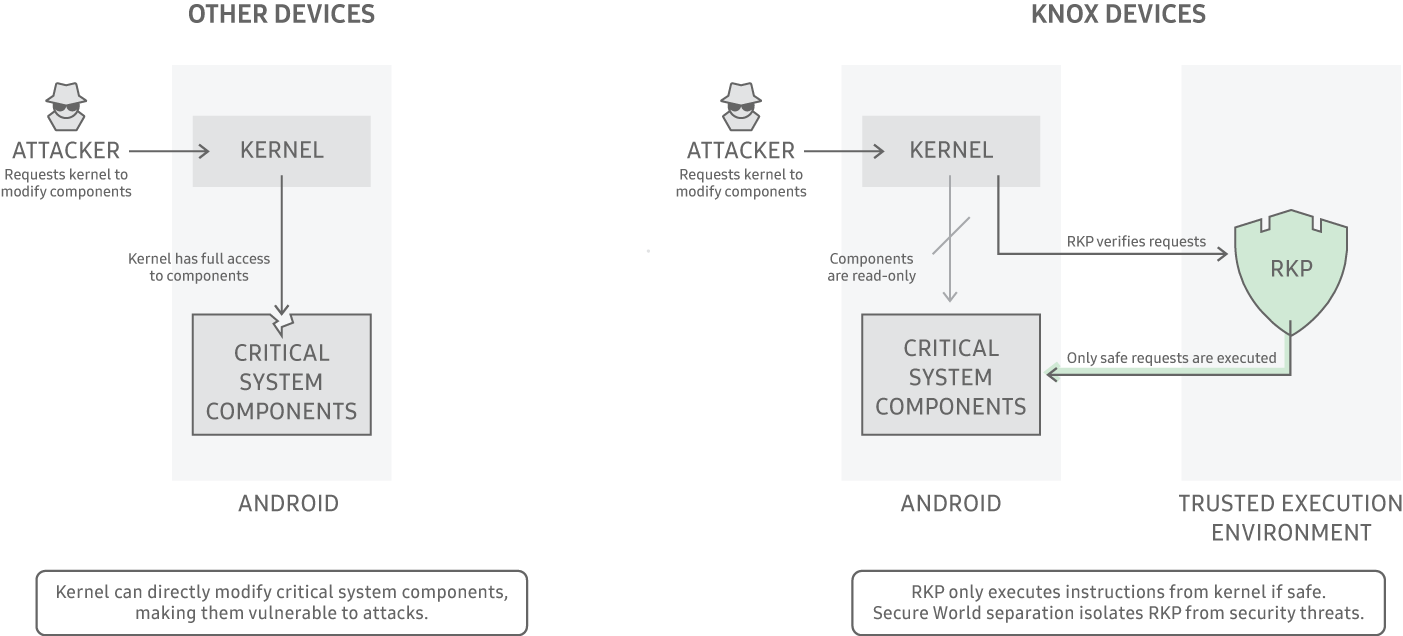
RKP’s isolation from the kernel shrinks the Trusted Computing Base (TCB) and helps secure it from attacks designed to compromise the kernel. This unique ability enables RKP to detect and prevent the most common kernel attacks. RKP protections are grouped into three areas:
- Kernel code – RKP prevents modification of kernel code and logic.
- Kernel data – RKP prevents modification of critical kernel data structures.
- Kernel control flow – RKP prevents Return-Oriented Programming (ROP) and Jump-Oriented Programming (JOP) attacks that reuse existing kernel logic to piece together exploits from the kernel’s own code.
How is kernel protection possible?
RKP uniquely employs a kernel security monitor within an isolated execution environment.
Running within an isolated execution environment would normally compromise a security mechanism’s ability to see into the kernel and monitor activities at runtime. However, RKP succeeds by utilizing patented techniques to control device memory management and by intercepting and inspecting critical kernel actions before allowing them to execute.
With RKP, customers can significantly reduce the severity of kernel attacks and limit the effectiveness of exploits that would typically cripple a mobile device.
Full security coverage
Each year, Samsung’s research and development teams add the latest runtime protections to a growing list of unique capabilities found only within RKP.
Although RKP is only one piece of Samsung’s holistic security solution, it successfully demonstrates the unique security guarantees possible when combining hardware, software, and advanced security research. Ensuring security claims are low maintenance, highly effective, and industry-leading is what provides enterprise customers the trust they need to deploy mobile devices in high-security environments.
Sources: Samsung



